Operational Overview
BlackOps Market was architected to address the critical vulnerabilities inherent in legacy darknet marketplaces. Launched in early 2024, the platform employs a zero-trust security model that mandates strict cryptographic verification for all participants. Unlike predecessors that prioritized volume over security, the blackops official infrastructure places operational security (OpSec) as the primary directive.
The platform operates exclusively on the Monero (XMR) blockchain. This decision eliminates the traceability risks associated with Bitcoin and other transparent ledger cryptocurrencies. By leveraging Monero's ring signatures, stealth addresses, and RingCT, every transaction on the blackops market link network remains mathematically opaque to external analysis.
Resilience is maintained through a distributed onion service architecture. The blackops market onion services are load-balanced across geographically dispersed nodes, ensuring resistance against DDoS attacks and network partitioning. This robust backend supports a thriving ecosystem of over 280,000 verified users seeking reliable, encrypted commerce channels.
Interface Verification
Reference imagery for the authentic BlackOps interface to prevent impersonation.
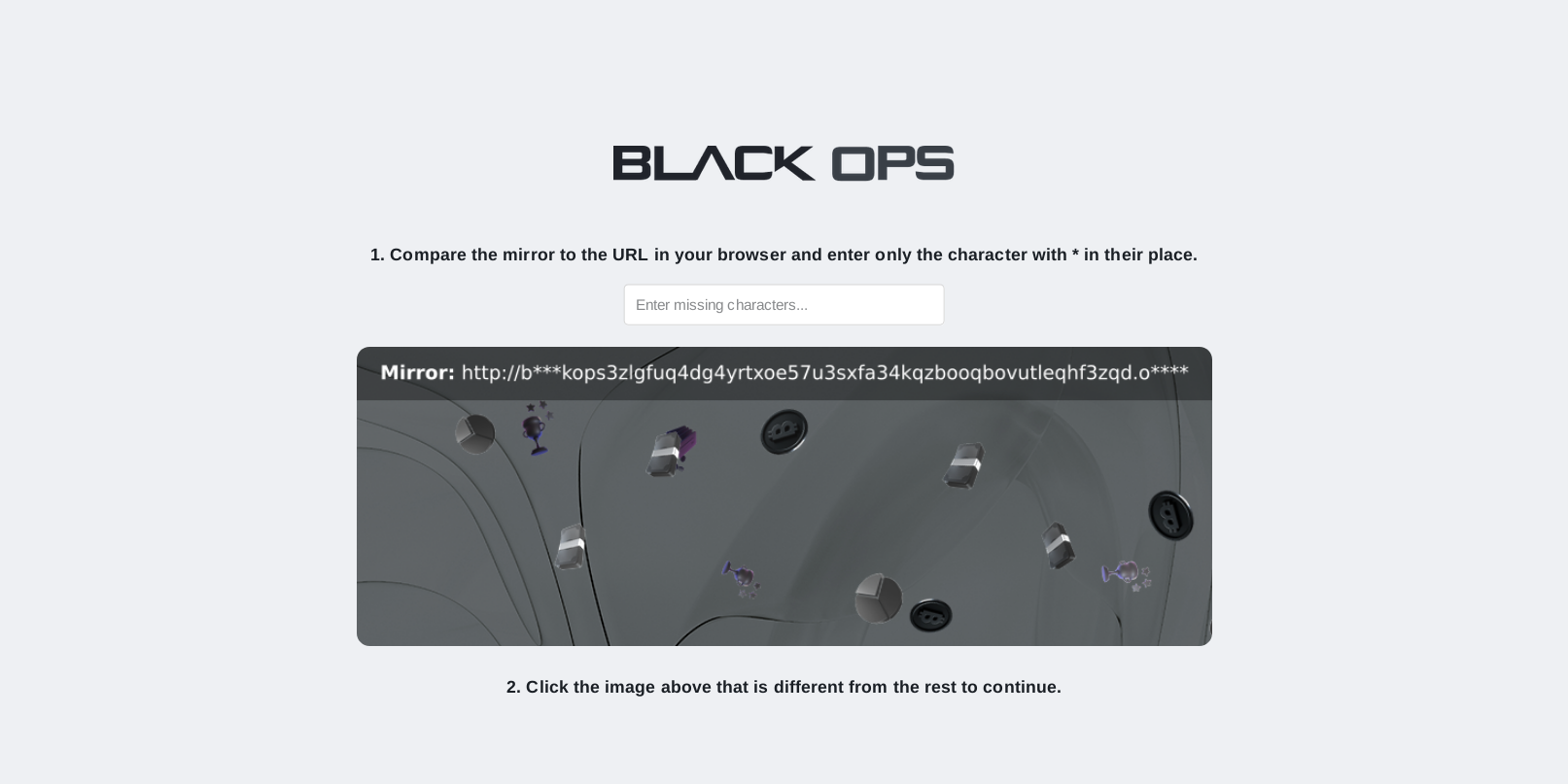
Fig 1.0: DDoS Challenge & Queue

Fig 1.1: PGP 2FA Login Gateway
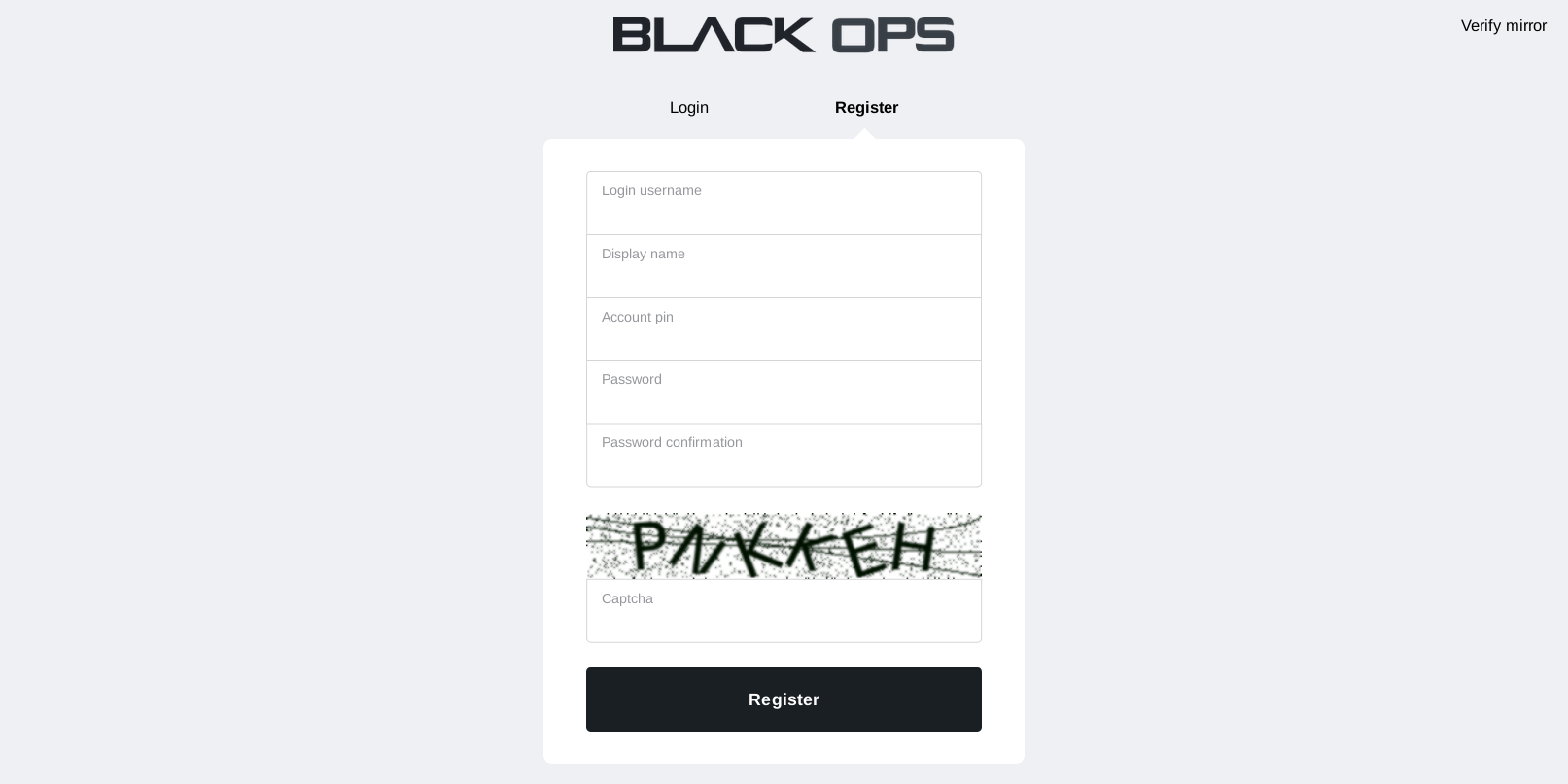
Fig 1.2: Encrypted Registration
Fig 1.3: User Dashboard & Wallet
Technical Specifications
Cryptographic Defense
- ▪ RSA-4096 Mandatory PGP
- ▪ Forced 2-Factor Authentication
- ▪ End-to-End Encrypted Messaging
- ▪ Metadata Stripping on Uploads
XMR Infrastructure
- ▪ Monero (XMR) Exclusive
- ▪ Integrated Wallet Auto-Sweep
- ▪ Subaddress Generation Per Order
- ▪ No On-Site Hot Wallets
Vendor Management
- ▪ Strict Vetting Procedures
- ▪ Bond Enforcement ($1000+)
- ▪ Performance Analytics Suite
- ▪ Access Control Lists (ACL)
Account Protocols
Buyer Anonymity BlackOps Market enforces a strict no-log policy regarding IP addresses and access times. Buyer accounts require only a username, password, and PGP public key. No external email or identification is ever requested. The system is designed to retain zero personally identifiable information (PII).
Vendor Tiering
The market employs a meritocratic vendor tier system. New vendors face restrictions on "Finalize Early" (FE) privileges until trust metrics are met.
> Tier 1: Standard Escrow (Default)
> Tier 2: Reduced Fees (150+ Sales)
> Tier 3: FE Enabled (300+ Sales, 4.9/5.0 Rating)
Escrow Logic
Multi-Signature Escrow Funds are held in a secure, intermediate state on the blockchain during the transaction lifecycle. The blackops market verified escrow system prevents vendor exit scams by ensuring funds are not released until buyer confirmation or automated timer expiry (7-14 days).
Dispute Arbitration In the event of a transaction dispute, the platform activates a mediated chat channel. Administrators review shipping evidence, PGP-signed communications, and blockchain data. Decisions are final and binding. The system favors evidence-based claims over reputation alone.
The Philosophy of Defense
Security on the darknet is not a product; it is a process. BlackOps Market operates on the principle that every user is a potential target and every connection is potentially compromised. Therefore, we do not rely on user discretion—we enforce security at the protocol level.
Our exclusive integration of Monero ensures that the financial graph of the market cannot be mapped. Unlike Bitcoin mixers which are statistically vulnerable, Monero's protocol-level privacy provides fungibility and deniability. Combined with mandatory PGP encryption for shipping details, BlackOps creates a compartmentalized environment where data leaks are mathematically improbable.
Encryption Standards
- Asymmetric RSA-4096 / Ed25519
- Transport Tor V3 Hidden Service
- Hashing SHA-256 / Argon2
- Currency Monero (RingCT)